Arista is trusted and powers the world’s largest data centers and cloud providers based on the quality, support and performance of its products. The experience gained from working with over 7000 customers has helped redefine software defined networking and many of our customers have asked us how we plan to address security. To us, security must be a holistic and inherent part of the network. Our customers have been subjected to the fatigue of point products, reactive solutions, proprietary vendor lock-ins and most of all, operational silos created between CloudOps, NetOps, DevOps and SecOps. By leveraging cloud principles, Arista’s cloud network architectures bring disparate operations together to secure all digital assets across client to IoT, campus, data center and cloud protecting them from threats, thefts and compromises.
Introducing Arista Zero Trust Security
Today’s introduction of our zero trust security vision is timely and important for our customers in appreciating the union of networking and security. In this decade, we need to eliminate the implicit trust associated with traditional network architecture and instead build secure, zero trust networks that assume devices only have access to resources they need and that once a device is on the network it is continuously monitored and detected for mal-intent. We are entering this third wave of security from prior eras of simple network access to end point protection to now: delivering a more holistic architecture for zero trust networking as shown in the figure below.
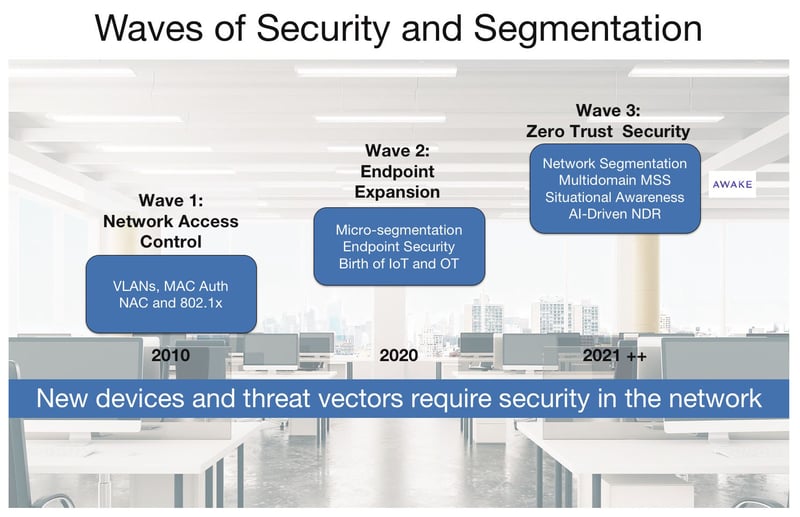
Patterned on the NIST guidance framework Arista’s zero trust security is based on three guiding pillars and principles:
- Network-based multi domain segmentation
- Situational awareness and visibility for all network resources
- AI-driven Network Detection and Response (NDR)
Arista’s Multidomain Segmentation
The foundation of a good zero trust strategy requires proper segmentation controls for multiple domains across client to data center to campus to cloud networks.
In the 2000-2020 era, the historical and simplest form of segmentation was port-based Access Control Lists (PACLs), VLANs or VXLANs with Routed ACLs (RACLS) and VRFs to regulate client communications. Of course, firewalls are used at the network perimeter for protection from external connections as well as in the data center for protecting east-west connections. Clearly, the concept of segmentation itself is not new as administrators have been grouping clients and workloads into VLAN or VRF segments since the early 1990s.
Granularly segmenting campus and data center networks requires a different approach especially with the growth of IoT and OT. Arista’s zero trust model goes beyond legacy segmentation models to offer security administrators more granular and dynamic segmentation groupings to accommodate the proliferation of devices and provides control as close to the user or device edge as feasible. A key requirement is that security segmentation groups need to be defined independent of network IP addressing constructs. In this world of networked IoT, a camera should only communicate with the DVR and security administrator. Security and network administrators need to have the ability to easily define, classify and group segments concerning who is accessing what, independent of IP addressing and other network protocol constructs.
Multi-Domain MSS - Next Frontier
The Arista Multi-Domain Macro-Segmentation Services builds upon the MSS® (Macro-Segmentation Service) journey we began five years ago. Today we are taking the next step and building upon Arista’s MSS with firewall partners with Arista’s new Group Segmentation MSS-Group,applying authorization to security segment groups in addition to interfaces, subnets or ports. MSS-Group is defined on a per segment group basis and can be created independently from IP addressing. The ability to create and enforce security segments between segments is a novel and powerful step offered in Arista switch's platforms with EOS® (Extensible Operating System). Unlike proprietary solutions, the MSS-Group segmentation architecture does not rely on proprietary Ethernet tags or protocols. The upstream and downstream leaf or spine switches can be mixed and matched across multiple vendors. Arista MSS-Group capable switches are agentless and can be deployed across client to campus to cloud in network wide rollouts, orchestrated via CloudVision®.
Situational Awareness Delivers Visibility
To complement network segmentation and protection, Arista provides situational awarenesswith established strategic partnerships and embedded technologies for broad visibility. Examples include:
- Profiling or authenticating devices using network-based analytics is particularly important for IoT devices that do not leverage 802.1X or device authentication.
- IoTvision. Profiling connected endpoints classifying devices into various groups such as Android, Apple, Amazon Echos, etc. along with associated information on their IP / MAC address via Device Analyzer.
- CloudVision Wi-Fi for wireless devices via its client journey to determine not only the type of device but the applications quality of experience as well. One can immediately identify what endpoints are running a particular application and how that application is performing across the user-base
- Arista Awake EntityIQ for behavioral device identification via an AI-based security knowledge graph that identifies, profiles and tracks devices, users and applications on an enterprise network.
- Arista DANZ Monitoring Fabric (DMF) can provide contextual insights across the cloud network working closely with Awake NDR for exchange of information.
AI Driven Continuous Network Detection & Response (NDR)
The third pillar of Arista zero trust security is based on continuous monitoring to identify malicious intent originating from both outside and inside the perimeter. Threats and risk scores surfaced by the Awake NDR platform can then be used to make segmentation decisions. Just because a device or user is on the network, does not imply it is to be trusted. The Awake Security Platform is built on deep network analysis across the campus, IoT and cloud networks. This new network detection and response (NDR) offering parses over three thousand protocols and processes layer 2 through layer 7 data, including performing encrypted traffic analysis. Awake’s Adversarial Modeling™ capability hunts for complex threats autonomously working in tandem with Ava™, the AI-driven security expert system, performing autonomous threat hunting and incident triage.
The Road Ahead in Security
As we enter 2021, it is clear that attacks are getting more lethal and the network must identify, protect and secure itself from bad intentions. Using our latest multidomain segmentation techniques, advanced crypto and encapsulations, artificial intelligence, and human expertise, Arista is proud to up the ante with zero trust security. We are securing cognitive campus workspaces with MSS-Group segmentation simplifying the access and permissions between users and networks. The ability to cope with the massive device proliferation requires the network to autonomously connect the dots across many dimensions of users, devices, access, time, entities, and protocols.
We are excited and welcome you to the 2021 era of proactive zero trust security with our preferred technology partners. It’s the right time to unify network and security!

/Images%20(Marketing%20Only)/Blog/Jayshree_Ullal_024.png)



Opinions expressed here are the personal opinions of the original authors, not of Arista Networks. The content is provided for informational purposes only and is not meant to be an endorsement or representation by Arista Networks or any other party.